Legal vendor due diligence is a crucial business process that companies must undertake to verify that third-party vendors can meet their compliance and legal obligations. The legal vendor due diligence process is a comprehensive review of a vendor’s risk and compliance practices that takes place before initiating a transaction or engagement. It’s a necessary risk mitigation process that protects businesses and organizations from security risks, compliance and regulatory violations, and operational losses.
As businesses and organizations turn to vendors and partners for technology solutions, data processing, and many other aspects of their operations, a failure on the vendor’s part to maintain compliance, data privacy, security, and ethical standards can leave the hiring company at risk for significant financial, reputational, and other losses.
Consider the case of an advisory firm that hires a subcontractor to perform an essential business function but fails to conduct any compliance due diligence. If the firm’s clients suffer any financial or regulatory losses, the firm will be liable for failing to vet their vendors adequately. Legal vendor due diligence enables organizations to identify these risks upfront, verify compliance, and establish trust-based vendor relationships built on transparency.
Smart organizations understand legal vendor due diligence is a vital business process, not a burdensome formality or checklist. The potential consequences and liability of vendor due diligence are too high not to take proper evaluation measures.
What is Legal Vendor Due Diligence?
Legal vendor due diligence is a systematic process for evaluating third-party vendors to identify legal risks before entering business relationships. This approach helps companies avoid costly legal issues and regulatory violations.
Legal vendor due diligence relies on three principles: risk assessment, regulatory and legal compliance, and ongoing vendor management and monitoring. These principles establish clear objectives for risk assessment, ensure compliance with applicable legal frameworks, and create structured processes for managing vendor relationships.
The main objective is to identify and mitigate risks. Legal teams review vendors' compliance history, contractual obligations, liability exposure, intellectual property rights, data protection practices, and regulatory standing to assess their suitability.
Sellers often hire financial and legal advisors to conduct vendor due diligence services. This practice is standard in transactions involving multiple potential buyers.
Key objectives include:
- Identifying legal compliance gaps
- Assessing regulatory risk exposure
- Evaluating contractual terms and conditions
- Reviewing insurance coverage and liability protection
- Analyzing dispute history and litigation risks
Legal Frameworks and Regulatory Requirements

Organizations must navigate complex regulatory environments during vendor selection and evaluation processes. Varying industry requirements demand tailored approaches to legal due diligence.
Financial services companies are required to comply with banking regulations, anti-money laundering laws, and consumer protection standards. Healthcare organizations must comply with HIPAA requirements and medical device regulations. Technology companies deal with data privacy laws and software licensing requirements.
Due diligence processes include legal, product, supplier, and tax considerations. Legal liability is only one aspect of a comprehensive vendor evaluation.
Regulatory compliance requirements differ by jurisdiction. International operations necessitate consideration of multiple regulatory frameworks, requiring specialized legal expertise and a systematic evaluation.
Common regulatory areas include:
- Data protection and privacy laws
- Industry-specific regulations
- Anti-corruption and bribery statutes
- Employment and labor standards
- Environmental compliance requirements
Third-party suppliers in regulated industries face increased scrutiny. Regulatory bodies expect companies to maintain robust vendor management programs with documented due diligence procedures.
Lifecycle Approach to Vendor Evaluation
Legal vendor due diligence includes ongoing monitoring throughout the business relationship, not just initial selection. This lifecycle approach ensures continuous compliance and risk management.
Initial Assessment
The initial assessment phase includes a comprehensive legal review before contract execution. Legal teams evaluate vendor credentials, compliance history, contractual terms, insurance coverage, and liability allocation to ensure a thorough assessment of the vendor's capabilities.
Ongoing Monitoring
Ongoing monitoring involves periodic compliance reviews and performance assessments. Organizations track regulatory changes and monitor news for potential legal issues.
Technology due diligence criteria can apply to various investment decisions. Mastery of these criteria allows organizations to tailor their approach to different vendor types and risk profiles.
Contract Renewal
Contract renewal requires updated due diligence reviews. Legal teams reassess vendor compliance and evaluate new risk factors that may have emerged.
Vendor due diligence requires systematic documentation and regular updates. Organizations maintain current legal assessments and compliance documentation to support ongoing risk management.
Key Assessment Areas and Risk Categories

Legal vendor due diligence requires a systematic evaluation across four critical domains that determine the viability of a partnership.
These assessments focus on financial stability, regulatory compliance, operational continuity, and potential reputational risks that could impact business relationships and operations.
Financial Health and Stability
Financial stability underpins vendor reliability and the success of long-term partnerships. Organizations must identify and address operational risk and deficiencies that could affect vendor performance.
Liquidity ratios provide immediate insight into a vendor's ability to meet short-term obligations. The current ratio should exceed 1.2, while the quick ratio should remain above 1.0 for most industries.
Cash flow analysis indicates operational efficiency and sustainability. Vendors with consistent positive cash flow over three years demonstrate greater reliability.
Revenue concentration is a risk when a single client accounts for more than 30% of total revenue, creating vulnerability to sudden contract terminations.
Credit ratings from agencies such as Moody's or S&P provide independent assessments of a company’s financial health. Vendors rated below investment grade require enhanced monitoring and oversight.
Compliance and Regulatory Checks
Regulatory compliance verification prevents organizations from inheriting vendor-related legal risks. Comprehensive due diligence establishes a baseline compliance status.
Screening against OFAC, EU, and UN sanctions lists identifies prohibited business relationships. Automated systems should verify beneficial owners, executives, and key personnel monthly to ensure ongoing compliance.
PEP screening identifies potential corruption risks and regulatory scrutiny. Enhanced due diligence is required when vendors employ current or former government officials. Vendors must also maintain robust anti-money laundering programs.
Key indicators include:
- Written AML policies updated within 24 months
- Regular employee training documentation
- Independent compliance testing results
- Suspicious activity reporting procedures
A history of regulatory fines over the past five years demonstrates the vendor’s commitment to compliance culture and effective risk management. Fines over $100,000 or repeated violations require detailed investigation.
Enhanced due diligence (EDD) is necessary for vendors in high-risk jurisdictions or industries. EDD involves additional documentation and ongoing monitoring.
Operational Resilience and Business Continuity
Operational resilience ensures vendors maintain critical services during disruptions. Business continuity planning is a core component of vendor assessments.
Business continuity plans must include detailed recovery procedures for disruptions. Plans should be tested at least annually, with documented results and improvement actions.
Disaster recovery plans should specify:
- Recovery time objectives under 24 hours for critical systems
- Recovery point objectives with a maximum 4-hour data loss
- Alternate processing sites with geographic separation
- Communication protocols for stakeholder notification
Backup systems and redundancy prevent single points of failure. Vendors should maintain duplicate infrastructure in separate locations with automated failover to ensure uninterrupted service.
Cybersecurity frameworks, such as ISO 27001 or NIST, provide structured approaches to information security. Vendors should demonstrate compliance through independent audits and certifications.
Supply chain dependencies create cascading risks if vendors rely on critical third-party providers. Mapping these relationships helps identify potential disruption sources.
Reputational and Ethical Risk Factors
Reputational risk assessment protects organizations from associations with vendors under public scrutiny or ethical concerns.
- Media monitoring provides early warning of reputation issues. Systems should track vendor mentions across news sources, social media, and regulatory announcements. Negative coverage patterns indicate potential reputational risks.
- Leadership background checks reveal past legal issues, bankruptcies, or ethical violations among key executives. Criminal history or regulatory sanctions can create ongoing risks.
- Environmental and social practices influence vendor selection. Poor labor practices or environmental violations can generate negative publicity and regulatory scrutiny.
- Litigation history analysis identifies patterns of legal disputes that may indicate operational or ethical issues. Active lawsuits over $1 million require detailed review.
- Industry reputation influences partner perceptions. Vendors with poor standing among peers present ongoing relationship risks.
- Documented ethical standards, such as codes of conduct and compliance certifications, demonstrate a commitment to responsible business practices. Regular ethics training and reporting mechanisms indicate mature governance.
Security, Privacy, and Data Protection Standards
Vendors must comply with established cybersecurity frameworks and data protection regulations. Companies should verify encryption standards, incident response procedures, and monitoring capabilities to protect sensitive information.
Cybersecurity Controls and Frameworks
ISO 27001 certification provides a framework for effective information security management. Vendors must implement controls to protect data assets. Companies should verify active certification status and review implementation details.
SOC 2 Type II reports evaluate security controls over time, examining five trust principles: security, availability, processing integrity, confidentiality, and privacy. Type II reports are more valuable than Type I because they test controls over extended periods.
Key cybersecurity controls include:
- Access controls and user authentication
- Network security and firewall configurations
- Physical security measures
- Regular vulnerability assessments
- Employee security training programs
Companies should conduct security audits at least annually, although some circumstances warrant more frequent assessment. Third-party assessments provide independent validation of vendor security. Companies must request current audit reports and remediation plans for any weaknesses.
Data Protection Regulations and Privacy Laws
GDPR compliance applies to vendors processing data of EU citizens. The regulation requires explicit consent, data minimization, and breach notification within 72 hours. Privacy risks in mergers and acquisitions are more complex when vendors operate in multiple jurisdictions.
HIPAA governs healthcare information protection. Vendors handling protected health information must sign business associate agreements and implement administrative, physical, and technical safeguards.
CCPA protects California residents' personal information. Vendors must provide data deletion rights, disclose data sales, and offer opt-out mechanisms. The law applies to businesses meeting certain revenue or data processing thresholds.
Critical compliance elements include:
- Data classification and handling procedures
- Consent management systems
- Data subject rights fulfillment
- Cross-border transfer mechanisms
- Privacy impact assessments
Incident Response and Breach Notification
Vendors need documented incident response plans with clear escalation procedures. Plans should identify response team members, communication protocols, and containment strategies. Companies must review these plans during due diligence.
Breach notification timelines vary by regulation. GDPR requires notification to supervisory authorities within 72 hours.
State laws often require customer notification within specific time frames. Vendors must understand all applicable requirements.
The essential components of an incident response plan include:
- Incident detection and classification
- Internal and external communication procedures
- Forensic investigation capabilities
- Legal and regulatory notification processes
- Recovery and documentation of lessons learned
Testing includes simulated breaches and other readiness assessments to identify gaps in response procedures. Companies should request evidence of recent testing and results.
Ongoing Data Security Monitoring
Continuous monitoring systems detect threats in real time. Security information and event management (SIEM) tools collect and analyze log data for comprehensive security insights. Vendors should demonstrate active monitoring and threat detection procedures.
Encryption standards protect data at rest and in transit. AES-256 is standard for data at rest, while TLS 1.2 or higher secures data transmission. Companies must verify encryption implementation across all systems.
Ongoing data security monitoring requirements include:
- 24/7 security operations center coverage
- Automated threat detection systems
- Regular penetration testing
- Vulnerability management programs
- Security metrics and reporting
Vendor security questionnaires capture detailed security information. Data protection due diligence frameworks standardize assessment. Companies should use standardized questionnaires for consistent vendor evaluation.
Due Diligence Process and Best Practices

Effective legal vendor due diligence relies on structured checklists, risk-based scoring systems, and strong contract protections. Systematic assessment tools and continuous monitoring improve outcomes as vendor relationships evolve.
Building a Vendor Due Diligence Checklist
A comprehensive vendor due diligence checklist is essential for successful procurement. Legal teams should create standardized forms to capture essential vendor information across categories.
Core checklist categories include:
- Corporate structure and ownership details
- Financial stability and creditworthiness
- Insurance coverage and liability limits
- Regulatory compliance history
- Data security and privacy practices
- Business continuity plans
The checklist should address industry-specific legal requirements. Healthcare vendors need HIPAA compliance verification, while financial services require SOX controls documentation.
Companies must customize checklists for different vendor types. Software providers require different scrutiny than professional services firms. Third-party relationships need specific integrity assessments to identify compliance risks.
Procurement teams should update checklists annually to address new regulations and emerging business risks. The checklist must evolve with the legal landscape.
Risk Scoring and Assessment Tools
Risk scoring converts qualitative vendor data into quantitative metrics, helping legal teams prioritize resources and focus on high-risk relationships.
The table below breaks down the typical risk scoring factors.
A risk-based approach allows companies to apply different monitoring levels. High-risk vendors receive extensive reviews every six months, while low-risk vendors may only need annual assessments.
Automated tools calculate scores from vendor responses, reducing manual work and ensuring consistent evaluations across all relationships.
Companies should set clear score thresholds. Vendors scoring below the threshold may need to implement additional safeguards or risk exclusion from procurement.
Contract Negotiation and Legal Safeguards
Strong contracts protect companies from vendor-related legal risks. Key provisions should address liability, compliance, and termination rights.
Essential contract elements include:
- Indemnification clauses that shift liability to vendors for their failures
- Compliance warranties requiring adherence to applicable laws
- Audit rights allowing periodic vendor assessments
- Termination triggers for compliance failures or security breaches
Data protection provisions require special attention. Vendors handling personal information must agree to specific security standards and breach notification requirements.
Insurance requirements should match the vendor's risk profile. High-risk vendors need higher coverage limits and additional policies.
Service-level agreements establish measurable performance standards, helping identify problems before they become legal issues.
Contract terms should allow scalability as vendor relationships grow, since initial agreements may expand over time.
Ongoing Monitoring and Risk Reduction
Vendor relationships require continuous oversight beyond initial due diligence. Ongoing monitoring identifies emerging risks and continued compliance.
Effective monitoring programs include:
- Quarterly compliance certifications from vendors
- Annual financial health reviews
- Real-time alerts for regulatory violations
- Performance metric tracking against contract terms
Companies should set monitoring frequencies based on risk scores. Critical vendors may require monthly check-ins, while others may need only annual reviews.
Technology platforms can automate much of the monitoring process. These systems track vendor news and flag potential issues for legal review.
Risk reduction strategies should address identified problems promptly. Solutions may include contract amendments, additional safeguards, or replacing the vendor.
Documenting all monitoring activities protects companies during regulatory examinations. Clear records demonstrate proactive risk management.
Frequently Asked Questions
Legal due diligence involves examining contracts, compliance records, intellectual property rights, and potential litigation risks.
The process requires a systematic review of corporate structures, regulatory filings, and financial obligations to identify legal exposures before completing transactions.
What are the essential components of a legal due diligence checklist?
A comprehensive legal due diligence checklist includes corporate formation documents such as articles of incorporation and bylaws. These documents establish the company's legal structure and governance framework. Another critical component is contract review, including material agreements, customer contracts, supplier arrangements, and employment agreements.
Intellectual property verification involves examining patents, trademarks, copyrights, and licensing agreements to ensure compliance with applicable laws and regulations. Companies must provide proof of ownership and registration status for all IP assets. The litigation and regulatory compliance sections address pending lawsuits, regulatory investigations, and compliance with industry-specific regulations.
Environmental liabilities and insurance coverage also require thorough documentation. Financial obligations include outstanding debts, guarantees, and off-balance-sheet liabilities that could impact the transaction value.
How does the legal due diligence process unfold in mergers and acquisitions?
The legal due diligence process begins with outside legal counsel representing the acquiring company. Initial planning establishes the scope and timeline for the investigation. Document request lists are prepared and sent to the target company, typically covering five to seven years of corporate records and material agreements.
A virtual data room is established where the target company uploads the requested documents. Legal teams review these materials systematically according to predetermined categories.
Management presentations and Q&A sessions address gaps in documentation. Legal counsel identifies red flags and requests additional information as needed. Due diligence findings are compiled into reports that highlight material legal risks to inform the final negotiations and terms of the purchase agreement.
What types of legal due diligence can be conducted during a transaction?
Vendor due diligence represents one common approach where sellers hire their own legal counsel to prepare due diligence materials, which is particularly useful in transactions with multiple potential buyers. Buyer due diligence involves the purchasing party conducting its own independent legal review, allowing buyers to focus on their specific concerns and risk tolerance.
Mutual due diligence occurs when both parties conduct a thorough examination of each other's legal standing, a common approach in mergers of equals or complex joint venture arrangements.
Limited-scope due diligence targets specific legal areas, such as intellectual property or regulatory compliance, focusing on a particular aspect of these areas. This approach is often used for smaller transactions or when there are time constraints.
What specific aspects of a company are examined in a legal due diligence report?
Legal due diligence examines corporate governance structures, including board composition, shareholder agreements, and voting arrangements.
Legal structure analysis identifies owners and explains decision-making processes, including a review of employment agreements and non-compete arrangements. Reviewers examine material contracts for termination clauses, change-of-control provisions, and assignment restrictions.
Regulatory compliance encompasses environmental regulations, data privacy requirements, and industry-specific licensing requirements. Reviewers document government investigations and regulatory correspondence and analyze intellectual property portfolios for ownership, validity, and potential infringement. They also evaluate trade secrets and know-how protection measures.
Financial commitments encompass debt agreements, guarantees, and contingent liabilities that may impact the transaction or future operations.
How can one effectively summarize the findings of legal due diligence in a report?
Executive summaries highlight the most significant legal risks and deal-breaking issues first, ranking material findings by severity and potential financial impact. Risk categories organize findings into groups, such as litigation, compliance, contracts, and intellectual property, providing specific recommendations for addressing identified issues within each category.
Deal structure implications explain how legal findings affect purchase price, representations and warranties, and closing conditions. Escrow arrangements and indemnification provisions are detailed.
Action items outline the necessary steps each party must take before closing, including obtaining regulatory approvals, securing third-party consents, and completing document remediation, along with the timeline for each action item. Red flag sections highlight issues that could impede deal completion or necessitate substantial price adjustments.
What are the potential risks of insufficient legal due diligence in corporate acquisitions?
Undiscovered litigation can lead to unexpected costs and divert management's attention. Hidden regulatory violations may trigger government investigations and result in penalties even after the transaction is closed.
Intellectual property defects, such as invalid patents or trademark disputes, can reduce the value of technology acquisitions and remove competitive advantages. Contract assignment issues may void key customer or supplier agreements when control changes, which can significantly impact revenue streams and operational capabilities.
Environmental liabilities can expose buyers to cleanup costs and ongoing regulatory oversight. Financial statement misrepresentations discovered after closing can lead to purchase price adjustments, and buyers may bring fraud claims against sellers.
Key Takeaways
- Legal vendor due diligence protects companies from security risks and compliance violations when working with vendors or partners.
- Organizations must evaluate vendors' data protection standards, security measures, and operational procedures before sharing sensitive information to ensure data confidentiality, integrity, and security.
- A systematic assessment process enables companies to select reliable legal partners and reduce potential liability.
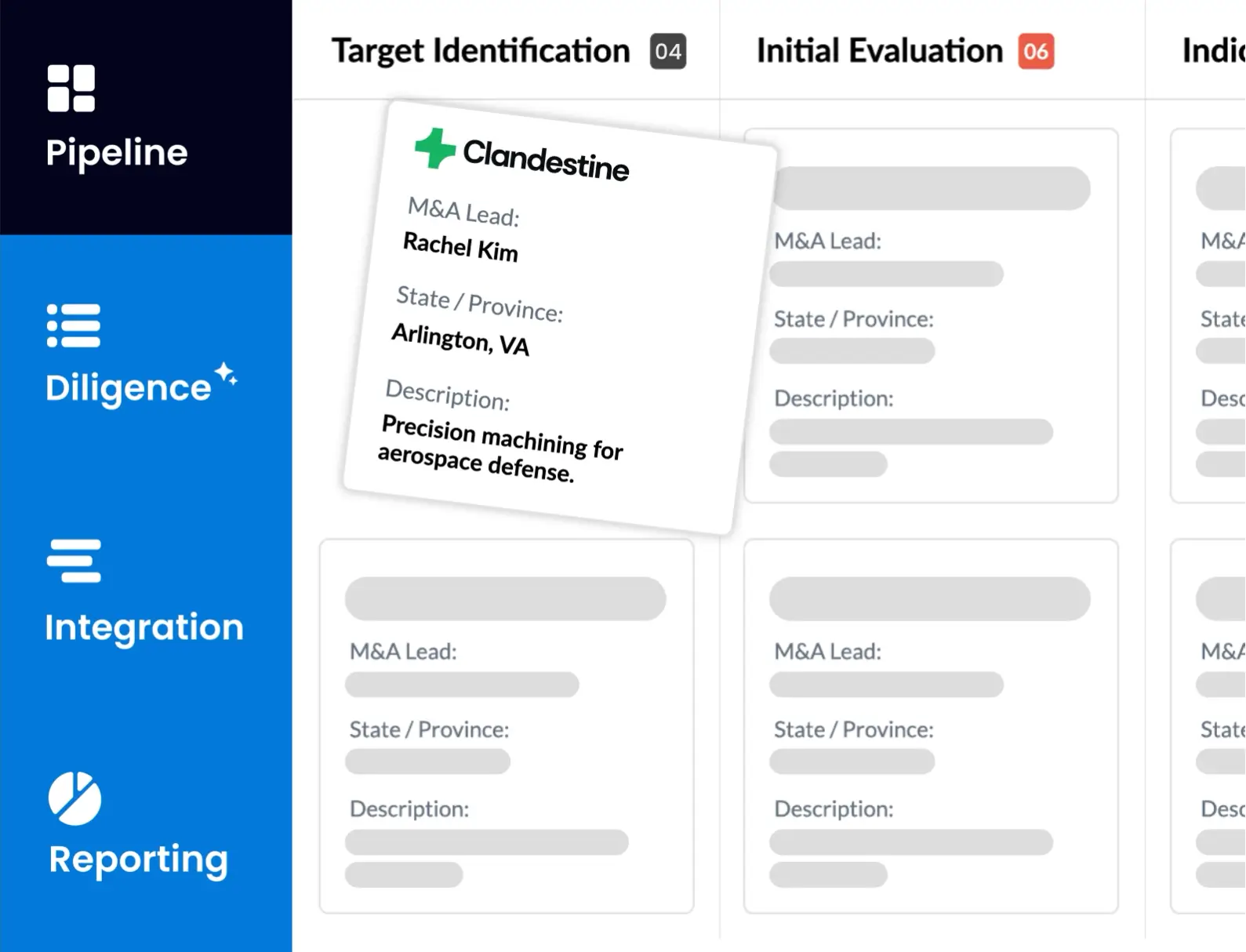
Legal vendor due diligence is a safeguard against legal, financial, operational, and reputational risk. The diligence process involves coordination across legal, compliance, procurement, and risk teams and requires access to accurate, up-to-date information. However, relying on spreadsheets, fragmented email threads, and disconnected document repositories makes managing this process challenging.
DealRoom’s M&A Platform streamlines the entire due diligence process by providing a centralized workspace for securely collecting, reviewing, and managing vendor information, such as risk assessments and evidence of compliance. Built specifically for complex legal and financial workflows, DealRoom enables teams to:
- Standardize due diligence checklists and automate repetitive tasks to speed up evaluations.
- Share sensitive documents securely with internal teams and external stakeholders, with granular permissions and access controls.
- Track progress and accountability with real-time dashboards, task assignments, and audit trails.
- Integrate ongoing monitoring by maintaining vendor records and compliance documentation in a unified system.
By combining secure data management with collaboration tools designed for diligence workflows, DealRoom can help organizations conduct more efficient, transparent, and defensible vendor evaluations, reducing time to completion while improving accuracy and compliance oversight.
Request a demo to see how DealRoom can modernize your legal vendor due diligence process.
















.avif)
.avif)
.avif)



.avif)
.avif)
.avif)




.png)
.png)
.png)
.svg)

.svg)
.avif)
