Hostile takeovers are in the news, with Paramount launching a hostile takeover bid to try to stop Netflix from acquiring Warner Brothers, and a lot of people have questions about hostile takeovers.
In this article, we'll focus on examples of companies that completed or at least attempted a hostile takeover of another firm and explain the reasons why.
What is a Hostile Takeover?
A hostile takeover occurs when an acquirer takes over a company without the consent of its management, instead side-stepping the management team to negotiate directly with the company’s shareholders. Hostile takeovers are generally launched after the formal offer has been rejected, and they are mostly applicable to larger public companies.
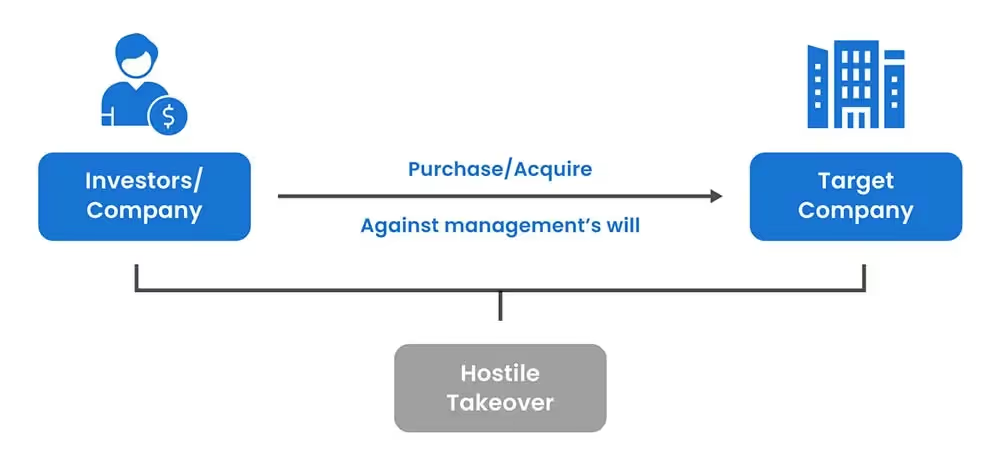
Examples of Hostile Takeovers over the years
Hostile takeovers have been a prominent figure in the business landscape over the years. Hostile takeover strategies have evolved due to broader economic conditions, and its impact on different industries have influenced broader market practices.
Some significant hostile takeovers through the years include when InBev took over Budweiser maker Anheuser-Busch and when Sanofi-Aventis took over Genzyme Corporation.
InBev’s acquisition of Anheuser-Busch
$52 billion
July 14, 2008
InBev was already the world’s largest brewer when it made an unexpected tender offer for Anheuser-Busch in June 2008.
InBev had a portfolio of beverages that included Stella Artois and Beck’s, and the notion that it was now going to add Budweiser to the list appeared to greatly appeal to industry investors: The shares of both companies rose on the news that InBev had made its approach.
Despite offering a 30% premium over the share price, the acquiring company’s offer was knocked back by the Anheuser-Busch directors. Ostensibly, this was because the price didn’t value their firm sufficiently. In reality, they were probably protecting their own interests.
Undeterred, InBev upped the stakes by making a direct approach to Anheuser-Busch’s shareholders, asking them to submit a motion to the company that would fire its board members and replace them with an alternative board.
In the end, there was no need: When InBev increased its offer to $70 a share, the Anheuser-Busch board - under pressure from no less than Warren Buffett, then an investor in the company - rescinded. In the end, maybe only Anheuser-Busch’s shareholders were the only ones to benefit.
While they gained a 40% premium over the share price, AmBev - the company formed by the takeover - has never thrived. At the time of writing over a decade later, its shares are priced lower than the time of the deal.
Oracle’s acquisition of PeopleSoft
$10.3 billion
December 13, 2004
PeopleSoft shares had been in free fall for nearly two years when Oracle first expressed an interest in an acquisition. From a high of $56, the shares were trading at around $15 in 2003.
When PeopleSoft made a bid to acquire a rival software firm, JD Edwards, for $1.7billion, Oracle CEO sensed the time was right to make his move. Before the JD Edwards deal was confirmed, Oracle had made an offer of $16 per share - a premium price of just 6%.
PeopleSoft’s current board squirmed. Probably still clinging to the notion that their company was worth closer to the original $52per share, they resisted the offer. And continued to do so for the following 18 months.
In fact, over that time, Oracle made ten separate offers, each one improving on the offer that preceded it. This lengthy and aggressive bid involved a proxy fight to gain control of the target company’s board by going straight through the target company’s shareholders.
With 60% of shareholders already willing to sell out to the hostile bidder, the PeopleSoft board finally gave in at $26.50 a share in December 2014.
For Oracle, this buyout was an undoubted success despite the hostile takeover defenses that prolonged the process: PeopleSoft probably was underpriced, even at the price that it eventually struck with shareholders.
In addition to making it the global number two in the business application software market behind German rival SAP, PeopleSoft’s annual fees from clients for maintenance and updates was even higher than it had initially thought. As one analyst said at the time: “You can only compete with size,” and Oracle managed that.
Sanofi-Aventis acquisition of Genzyme Corp
$20.1 billion
February 15 2011
The deal between Sanofi-Aventis and Genzyme Corp is regularly stated by textbooks as an example of a hostile takeover - possibly because a timeline of the deal leaves little doubt that a hostile takeover was the intention of Genzyme Corp from the outset.
Just one month after having an initial approach of $18.5 billion turned down by Genzyme’s board of directors, Sanofi-Aventis returned with the exact same offer. A case of “this is your last chance.”
On the Genzyme side, its CEO Henri Termeer informed Sanofi CEO Chris Viehbacher in a letter that the deal “drastically undervalued the company.”
No sooner had he done so than Vehbacher said that the offer might be taken direct to Genzyme’s shareholders. Shareholders initially backed Termeer, saying that they would only accept a bid for $75 per share(Sanofi’s opening gambit was $69 per share).
Eventually, five months after much back and forth between the two sides, Genzyme’s shareholders accepted a bid of $74 per share plus contingencies based on the company’s post-acquisition performance. That turned the potentially hostile situation into a friendly takeover.
When the deal closed, it gave Sanofi access to Genzyme’s patents for rare disease medicines, just as most of its own patent portfolio was expiring. To this day, the deal is the second biggest hostile merger in the biotech sector in history.
RBS and ABN Amro
$97 billion
10 October 2007
The 2007 takeover of Dutch bank ABN Amro by a consortium led by RBS could just as easily be listed under “disastrous acquisitions” and “be careful what you wish for” as hostile takeovers.
A key detail in the deal is one that its price may have been inflated by the fact thatBarclays was also trying to acquire ABN Amro at the same time. The fact thatRBS “succeeded” where Barclays failed is already being seen as a historical turning point for the two British banks.
In 2007, with the global banking industry already looking to be in the mid set of a bubble, RBS led a consortium that also included Belgian bank Fotis and Spanish bank Santander to acquire ABN Amro.
Perhaps riled by ABN Amro publicly stating that it preferred a deal withBarclays, it launched a hostile takeover bid. At a transaction price of $97billion, it was the biggest M&A transaction in the banking industry in history. Such honors rarely bode well.
In Q2 2008, the global financial crisis began and the rest is history. An inquest by the British government into the deal found that the RBS dealmakers relied on “two folders and a CD” for the deal’s due diligence.
The debt pile brought as a result of the deal severely damagedRBS and it has never truly recovered. It now operates under the Natwest umbrella. In 2008, it topped out at 5,900 points on the London Stock Exchange. In 2022, it hovers close to 250.
Microsoft and Yahoo!
$45billion
Date: Deal never closed
The fifth deal on our list is an example of a bear hug hostile takeover: Microsoft’s $45 billion acquisition of Yahoo! in 2008. When Microsoft went public with its first offer in February 2008, it had already been in informal discussions with Yahoo for the previous two years.
Yahoo! was seen as something of a basket case at the time, continuously shedding workers, issuing profit warnings, and generally showing an inability to offer any answer to Google’s domination of internet search.
Over the next two months, the publicity generated by Microsoft’s offer brought others on board, including Google, AOL, and NewsInternational. Yahoo! flirted with all four, only one of which (Microsoft)retained any interest. Apart from… shareholder activists.
In May, Carl Icahn and T Boone Pickens acquired a combined $1.25 billion in Yahoo! company’s stock in an attempt to force the board to sell to Microsoft.
It was all to no avail. The target company’s management instead entered a partnership agreement with Microsoft around internet advertising, which largely went nowhere.
The company was subsequently sued by its shareholders (led by Carl Icahn) who were able to prove that the board of directors had planned to reject Microsoft’s offer well in advance of it arriving, thus neglecting their fiduciary responsibility to shareholders.
Roche and Genentech
Another notable hostile takeover was the acquisition of Genentech by Roche in the biochemistry industry.
Genentech, Inc. is an American biotechnology corporation headquartered in South San Francisco, California. Swiss pharmaceutical company Roche made an offer to acquire all outstanding shares of Genentech for $89 per share in cash, which was a premium over the market price at the time. It was later raised to $95 per share, valuing the deal at approximately $46.8 billion.
To protect against Roche’s hostile takeover attempt, Genentech adopted a poison pill defense, which involved applying certain measures that would dilute the value of shares, making the acquisition more expensive and less appealing for Roche.
Despite this defense strategy, Roche pursued the acquisition by directly negotiating with Genentech's existing shareholders, bypassing the target company’s board of directors. This led to a successful takeover and the deal closed in March 2009.
As a result, Roche enhanced its position in the biotechnology field by combining their operational strengths with Genentech’s, and broadening their product pipelines. The acquisition was expected to generate substantial financial synergies, estimated to be between $750 to $850 million annually.
Elon Musk’s acquisition of Twitter
Elon Musk’s acquisition of Twitter technically started as a standard acquisition proposal. Elon became Twitter’s largest shareholder after acquiring a significant stake, but he didn’t disclose any intention of taking over the public company initially.
He delayed disclosing his 9% stake in Twitter until he submitted a takeover proposal in April of 2022, offering to buy twitter for $54.20 per share, which was a premium over Twitter’s stock price at the time. This valued the company at approximately $44 billion.
An incentive for Elon Musk to buy Twitter was to transform it into a place that better supports free speech. However, Twitter deemed Elon’s offer unsolicited and posed a threat to their independence, which is why the acquisition faced regulatory scrutiny from the U.S. Securities and Exchange Commission (SEC) and the Committee on Foreign Investment in the United States (CFIUS).
Twitter’s board tried to adopt a poison pill strategy for defense, making the company more expensive and less appealing. Elon complicated the acquisition further when he threatened to back out of the acquisition due to the spam and bot accounts concerns, giving the company a series of legal threats and potential lawsuits to face.
However, after enough negotiations and reconsideration of terms, the defense strategy was never activated, and the board finally approved of the takeover for $44 billion. The acquisition proceeded under the agreed terms, which ultimately led to Musk’s ownership of the company.
Bendix Corporation and Martin Marietta
If we go further back in history, there's probably no other deal that could top up the dramatic conflict between Bendix Corporation and Martin Marietta in 1982. It was worth remembering for the crown jewel defense that Martin Marietta used to make the company less attractive to Bendix by selling off its most valuable assets.
That was just the beginning of the drama! Martin Marietta turned the tables by launching a counter-takeover or what’s known as the “pac-man defense” against its own acquirer. The then prey now became the predator and began acquiring Bendix shares in the open market, aiming to gain control over Bendix itself.
The turmoil escalated when both companies went into a bidding war, attempting to purchase each other’s stocks. The situation created a complex and unstable condition in their voting power, as each company owned a significant portion of the other.
However, the tension finally came to an end when Allied Corporation (now part of Honeywell) chimed in as a white knight, offering a friendly takeover for Bendix. As part of the resolution to stabilize the situation, Allied also owned a major number of shares in Martin Marietta. Now both companies are under new management structures.
Why Hostile Takeovers Happen
Hostile takeovers happen because investors believe that companies are significantly undervalued, and that the current management lacks the competence to address what they perceive as a misvaluation.
Hence, they by step the management team, instead approaching the company’s shareholders about a takeover. The investors give the shareholders something to ponder: Are their shares undervalued, and if so, does the hostile takeover offer reflect the shares’ true value?
Understanding Hostile Takeovers
Hostile takeovers have probably gained an undeserved reputation owing to their name. If the same transaction was termed ‘Direct Shareholder Approach’ (which is effectively what a hostile takeover is), people might view them differently.
There is some debate over whether hostile takeovers add value or not, but one thing is certain: They increase focus.
A hostile takeover forces management and shareholders alike to focus and possible rethink some issues they may have been taking for granted. Questions that can arise during the process include: “are we implementing the wrong strategy?”; “is the company undervalued, and why?” and“could the situation be improved management team?”
The nature of hostile takeovers is that the target company is typically public. Over the past decade or so, they have gained some acceptance among activist shareholders - themselves avowed critics of company management - as they believe the hostile takeover will better reflect the company’s true value.
The Operating Reality
Even a potential threat of a hostile takeover causes the Target’s board to deploy “killer bees” and develop anti-takeover defenses. However, clarity on who to protect, when and how is a key consideration. Courts typically want to balance shareholder and management interest, but this is not possible all the time and often things skew to protecting management at the expense of shareholders.
Shareholders have also pressurized boards of companies like Hewlett-Packard and Bristol-Myers Squibb to weaken their anti-takeover defenses to ensure the balance does not tilt only towards the company management.
All publicly traded companies generally deploy at least one anti-takeover mechanism by adopting shareholder rights plans.
Frequently Asked Questions
What is a hostile takeover?
A hostile takeover happens when one company tries to acquire another without the target company’s approval. The bidder goes directly to shareholders or attempts to replace management to gain control.
What are some famous examples of hostile takeovers?
Well-known examples include Kraft’s takeover of Cadbury, Sanofi’s acquisition of Genzyme, and Oracle’s purchase of PeopleSoft. Each case involved aggressive bidding and public resistance from the target company.
What is the largest hostile takeover in history?
The largest hostile takeover to date is Vodafone’s $183 billion acquisition of Mannesmann in 2000. The deal reshaped the global telecom industry and remains one of the biggest corporate mergers ever completed.
Why do companies attempt hostile takeovers?
Companies pursue hostile takeovers to gain strategic assets, enter new markets, or remove inefficient management. They see potential value that current leadership might be overlooking.
How do companies defend against hostile takeovers?
Targets often use tactics such as poison pills, white knight defenses, or staggered boards. These strategies make the acquisition more difficult or expensive for the bidder.
Are hostile takeovers legal?
Yes, they are legal in most markets as long as the acquiring company follows securities regulations. However, they are often controversial and closely monitored by regulators.
What is the difference between a hostile and friendly takeover?
A friendly takeover happens when both companies agree to the merger terms. In a hostile takeover, the target company’s board rejects the offer, and the acquirer goes directly to shareholders or seeks control through other means.
















.avif)
.avif)
.avif)



.avif)
.avif)
.avif)




.png)
.png)
.png)
.svg)

.svg)
.avif)
