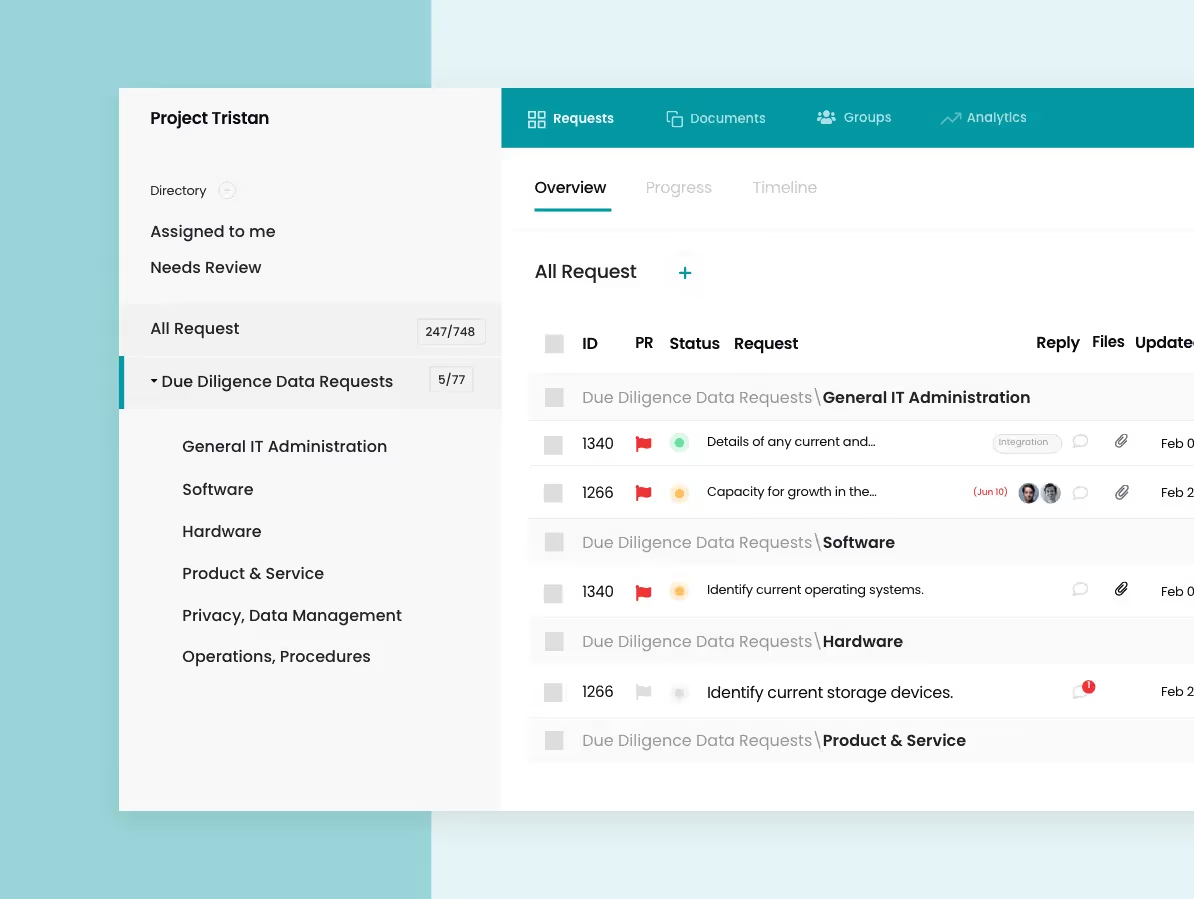
IT Due Diligence Playbook
This template focuses on the crucial IT aspect of M&A transactions. Prevent future IT complications by focusing on all the right areas such as data privacy management, customer support systems, cyber & network security, software, hardware and more. Book a playbook demo to explore — schedule a call with us and we will reach out to help you get started.
- Technology architecture review
Evaluate infrastructure, software, data systems, and integrations to identify legacy risks and value-unlocking opportunities. - Cybersecurity & compliance readiness
Assess security protocols, access controls, and compliance with standards (e.g., ISO, SOC, GDPR) so you can mitigate IT-related deal risks. - Data migration & system rationalisation
Map out system overlaps, migration paths and retire-or-retain decisions to streamline post-close tech consolidation. - Cross-functional coordination
Bring IT, security, operations and business-unit leads together in one workspace where tasks, documents and comments stay aligned.
Complement your IT review with the Sell-Side Due Diligence Checklist for a full seller readiness scope, or start broadly with the Master Due Diligence Checklist to ensure all transaction-critical domains are covered.




.png)
.png)
.png)
.svg)

.svg)
.avif)
