In her book ‘Here’s how they tell me the world ends’, author Nicole Perlroth outlines a series of cyber threats that companies face on an ongoing basis.
In one example, known as zero-day, hackers break into a company’s devices and move around undetected. Needless to say, the consequences for companies can be extremely damaging.
When discussing an M&A transaction with another company, the threat posed by software bugs like zero-day and others makes cybersecurity due diligence an absolute necessity. This is true for companies of any size.
We at DealRoom help dozens of companies with diligence process and in this article, we delve a little deeper into cybersecurity due diligence and provide a checklist of how it should be conducted.
What is cybersecurity due diligence?
Cybersecurity due diligence is the process of anticipating, identifying, and addressing cyber risks across a company’s network ecosystem.
The aim of cybersecurity due diligence is to address the threats to network security that a company (and increasingly, its external stakeholders such as suppliers and partners) face.
Why is cybersecurity due diligence important?
The scale of the negative impact posed by hackers underlines the importance of cybersecurity due diligence. By some estimates, global cyber crime will cost companies over $10 trillion by 2025.
In addition to reducing these risks, cyber security due diligence enables companies to show that they’ve been compliant, reducing their exposure to regulatory fines for negligence in the area of cyber security.
{{widget-hsembed}}
Deals that collapsed over inadequate cybsersecurity
Research conducted by Forescout indicates that over half of participants in the M&A activity encounter critical cybersecurity risks in target companies that put deals in jeopardy.
A good example is provided by Facebook’s proposed takeover of Musical.ly (TikTok’s predecessor) in 2016. The deal fell through as a result of the company’s exposure to data risks in China, and its policies around the data safety of child users on the platform.
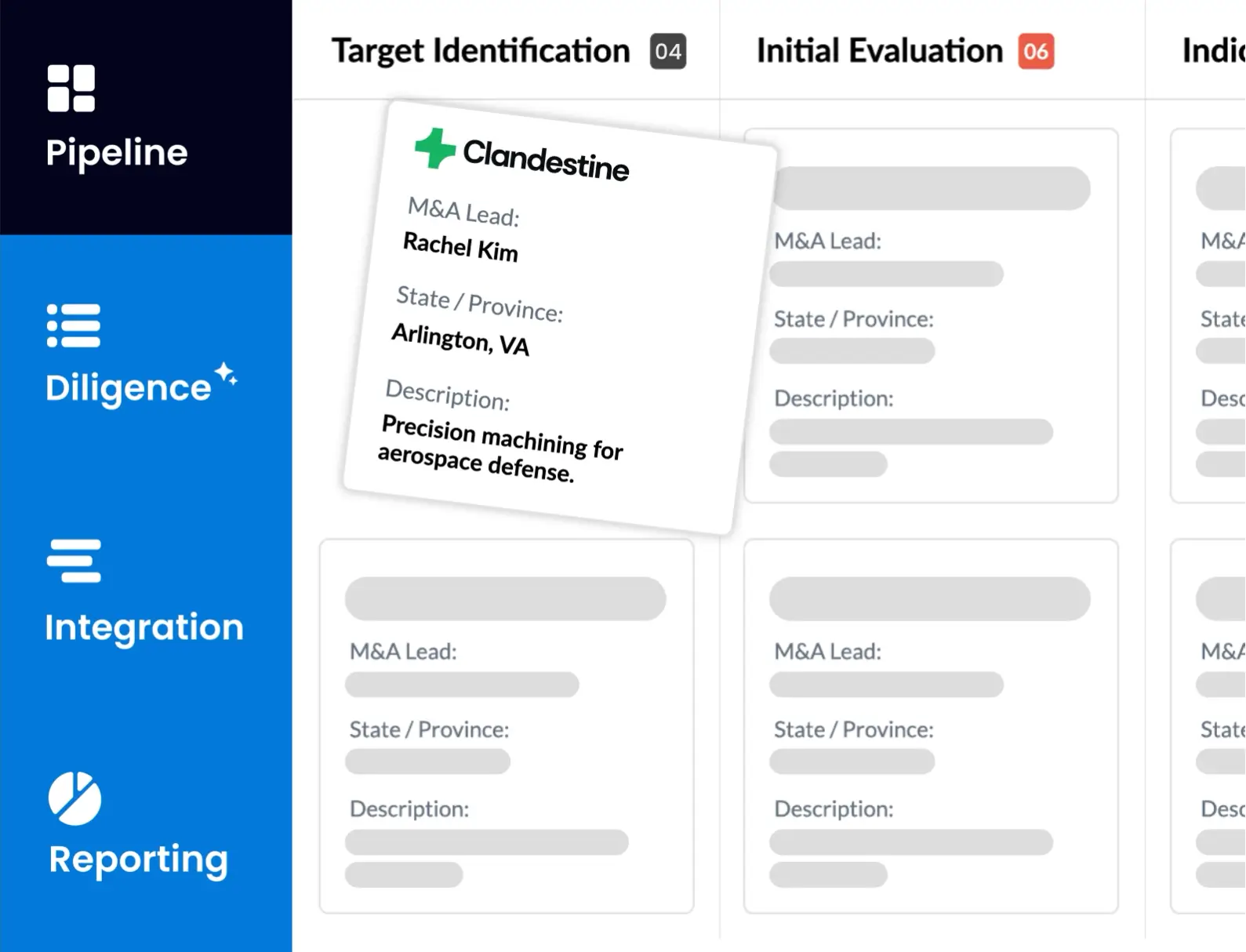
The cybersecurity due diligence checklist
NB: This list has been designed for companies considering M&A transactions, but many of the points mentioned could equally be applied to those simply looking to improve their own cyber security risks.
Talk to DealRoom today about how our due diligence platform can help you, regardless of which camp you fall into.
1. Conduct a risk profile of the acquisition target
- Consider the size and complexity of the business and its IT infrastructure, and its IT interfaces with third parties.
- Determine what control procedures (especially internal risk assessments) are carried out by the target and when the most recent such events took place.
- Assess the results of the latest cyber security procedures and what steps were taken to respond to its findings.
- Assess data ownership and historical data ownership of company.
2. Investigate legal standing of target company
- Understand the relationship between the company, its critical vendors, and the interfaces between them.
- Understand the regulations that the target company needs to follow (and if they are different to your own).
- Understand whether the company has obtained security licences of any form.
- Investigate whether the company has received any warnings of fines for FTC breaches, or any other regulatory body.
- .Understand who is responsible at the target company for dealing with the appropriate regulatory bodies.
3. Managing cyber security during the transaction
- Create an asset inventory that includes physical (laptops, cell phones, data rooms, etc.), logical, and software systems. Also pay particular attention to the managed services and the security measures taken with these services.
- Review the target company’s incident response plan, business continuity plan, and disaster recovery plan.
- Assess the performance of each of the plans in the light of previous cyber security issues (if any).
- Assess the target company’s vendor management program.
- Review the target's access management policies, business-wide password management platform and other tools used across the company for secure access management.
- Understand how the physical infrastructure and technology stack will integrate with your company’s own systems and the risks that can arise during the integration progress.
- Understand who controls and/or has access to data at the target company and how it manages the data of third parties.
- Assess which systems within the company have internet access, and to what extent this creates risks.
- Conduct an audit of the company’s physical infrastrucfture - e.g. access to data servers, cyber security measures on cell phones, facility safety controls, etc.

Bonus: Post-merger integration cybersecurity checklist
Integrating the target company’s IT systems safely
- Ensure that the two companies’ cyber security policies are fully aligned.
- Ensure that current and new employees are fully training in the cyber security procedures required and that they have signed up to these procedures.
- Assign people to manage cyber security as before, ensuring that they are aware of any changes that have occurred as a result of the merger or acquisition.
- Rewrite the company’s cyber security measures as appropriate to take into account risks identified at the target company.
- Schedule regular risk assessments for the company moving forward.

















.avif)
.avif)
.avif)



.avif)
.avif)
.avif)




.png)
.png)
.png)
.svg)

.svg)
.avif)
